With all the popular social networking websites there on the web, managing them from several different internet browser tabs or windows can get frustrated very quickly.
Besides our own Facebook Page, Twitter account, and Google+ profile, I also manage several others and, YES, I feel the “time management” pain!
To make social media management and monitoring easier for users, some very innovative desktop applications and mobile apps were developed to help organize multiple platforms and information sharing across selected networks.

Using online tools like TweetDeck, Seesmic, Hootsuite, Feedly, Twuffer and Buffer App for scheduling and posting directly from a web page has become an absolute necessity especially where Twitter is concerned.
Additionally these apps gives you the ability to post on one or all of your connected accounts together i.e Multiple Facebook, Twitter or Google+ profiles.
These applications don’t require your passwords for social media accounts, i.e. It would be really very uncool in sharing your Facebook password with a third-party site. That’s where OAuth comes in.
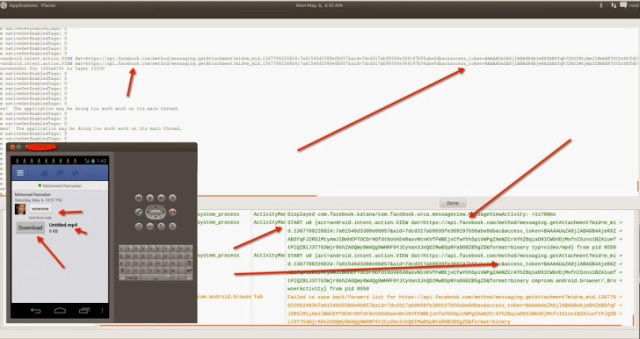
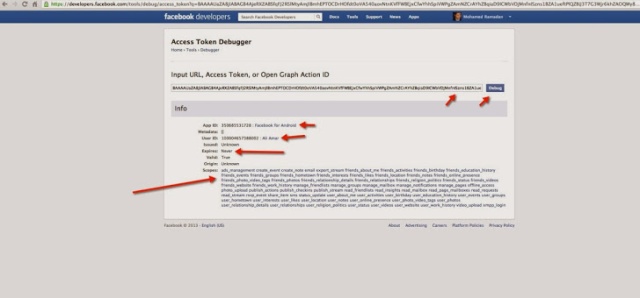
OAuth is an open standard for authorization, which keeps your passwords safe on third-party sites and instead of giving the keys to your entire house, you’ve given a special key called ‘Access token‘ that only opens one room which you want them to access.
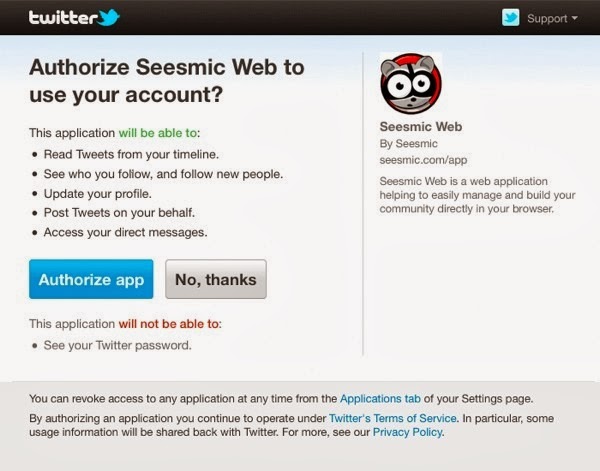
This Access token behaves similar to a session variable which you can store in a cookie to keep the user logged into your website. The only difference is that many services will send back an Access Token and Secret Access Token. You likely need both of these to pull any data from the server.
But more importantly, if somehow that application server gets hacked, your Twitter or Facebook passwords are still safe. But yes, the hackers would still be able to post on your behalf on Facebook or Twitter and can spread spam via tweets, status updates or Direct Inbox messages.
Rather than hacking into individual accounts which is almost impossible, Hacking an OAuth based application server, having millions of users – is enough to damage the Internet and Social Media.
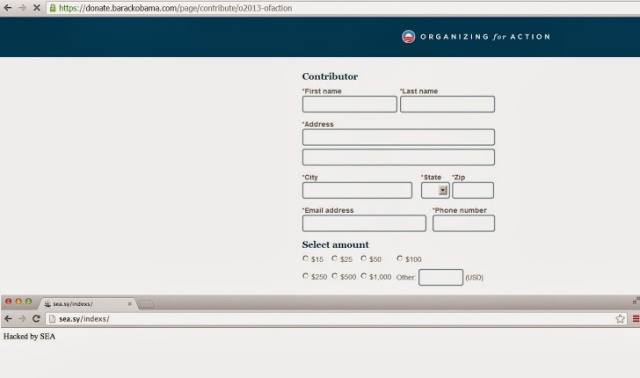
Just yesterday Buffer, the social content management and scheduling service was hacked by cyber crooks, which resulted in a flood of unauthorized posts to user accounts for both Twitter and Facebook.

The security of such apps should be very high, where access to Social media accounts of millions of users are available in bulk after exploiting the vulnerabilities in application server only. Buffer Hack was basically used to spread SPAM messages linked to weight-loss web site.
The main reason why this particular attack is so effective is because:
- The victims were essentially receiving messages including links from sources they trust; accounts that they follow on Twitter or Facebook.
- A hacker could trigger huge spam messages on all buffer users with one click.
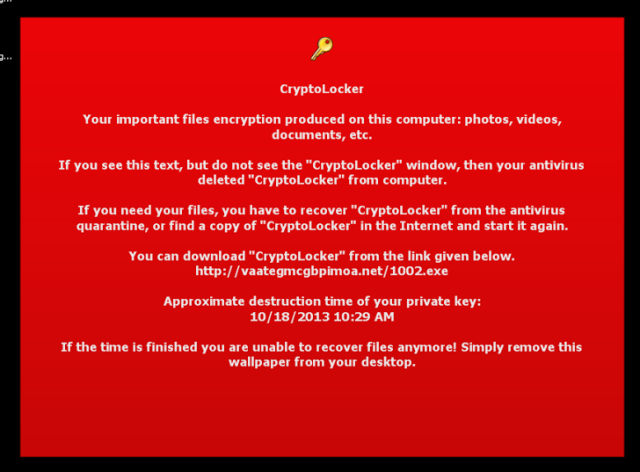
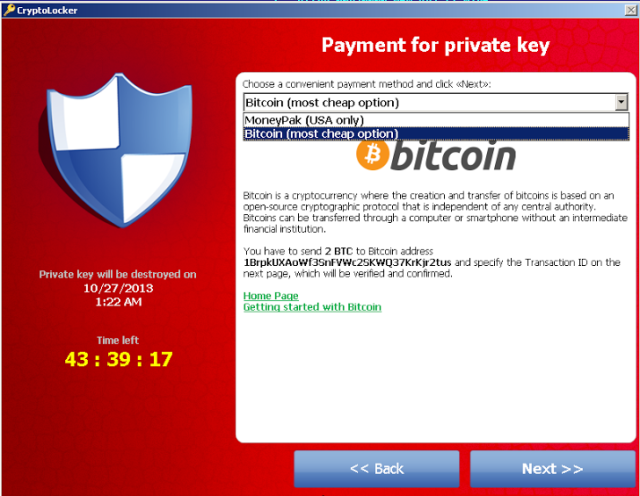
But in the worst scenarios, a malicious attacker could use the same techniques to spam links to Malware infected websites or other such websites serving exploit kits to compromise visitors’ computers.
After recovering for Security Breach, Buffer said on Sunday that they have encrypted all OAuth access tokens in the database for further security.
To avoid such issues, pay attention to the permissions that each app is taken from your account. If it does something you don’t want it to do, just don’t use that app.
There is no good or even half good way to protect keys that untrusted users can access. The minimum amount of effort won’t be effective. Even the maximum amount of effort won’t be effective against a skilled hacker with just a few hours of spare time.
It is a genuine problem with no effective solution. Not in Java, not in C#, not in Perl, not in C, not in anything. Think of it as if it was a Law of Physics. Your alternatives are:
- Always use trusted applications and grant limited required permissions.
- Turn your application into a service and run it on a machine that you control access to.
- Use some authentication mechanism that doesn’t require permanent secret keys to be distributed.
Always, be sure to regularly review your authorized apps so you don’t run into trouble if you haven’t used one of them in a while, you’re probably better off getting rid of it completely.
All you need to do is go to your Twitter settings and revoke access to that app. That way, your tokens become useless and your account is under your control again, without even having to change your password.

via The Hacker News http://thehackernews.com/2013/10/security-breach-at-oauth-based.html

![]()